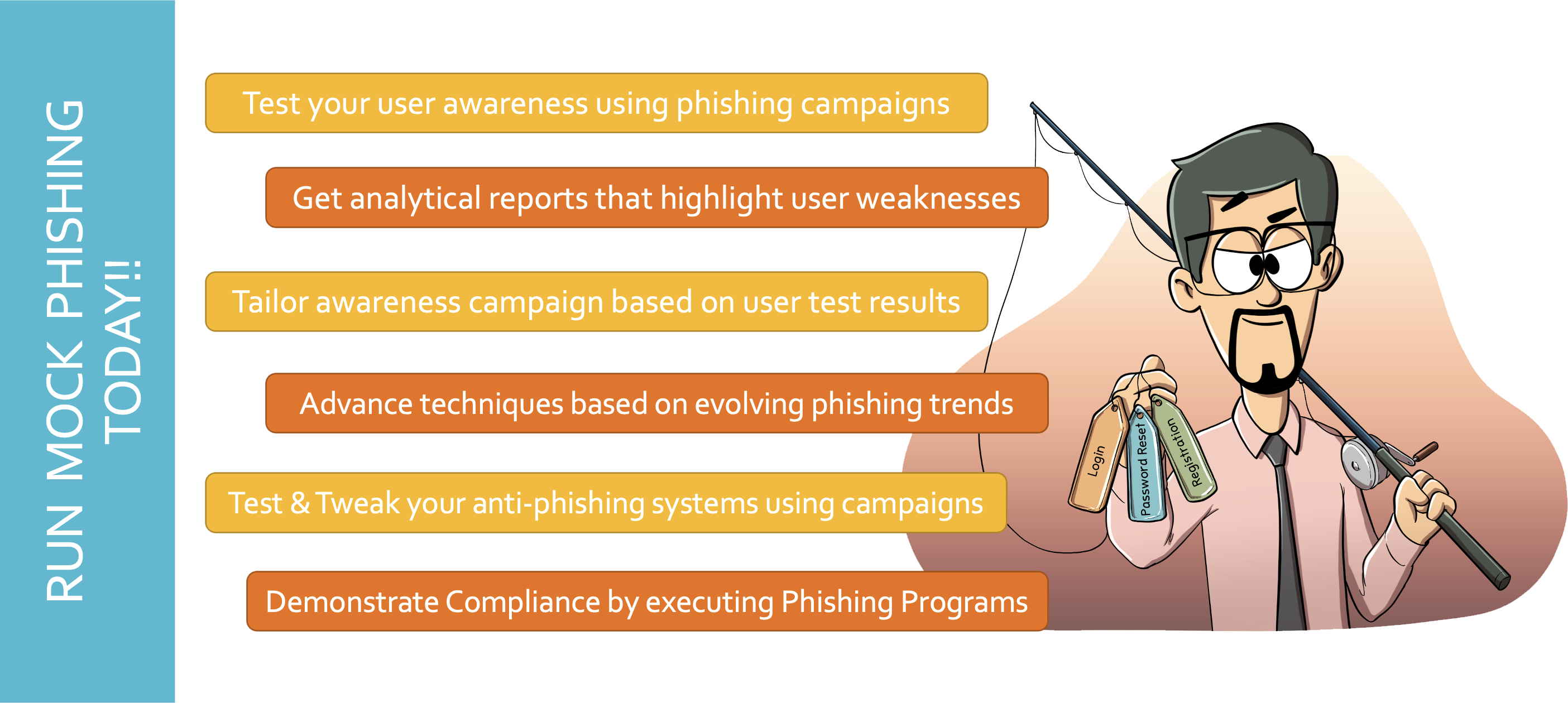
Salesforce Phishing Awareness
/*! elementor - v3.6.7 - 03-07-2022 */ .elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px} Salesforce Phishing Awareness Being in the spotlight does not get the attention of just the right audience but the wrong ones too. When it comes to CRM, Salesforce, the company, has quite literally taken the place of the actual definition of Sales Force. Googling for Sales Force, employees of a company responsible for selling...
Read More